Page 120 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 120
Information Security and Privacy
Notes At this point, the subject’s identity and the certificate’s integrity (no tampering) have been
verified. The certificate is typically combined with a signed message or signed executable file,
and the public key is used to verify the signatures (see digital signature and code signing). The
subject’s public key may also be used to provide a secure key exchange in order to have an
encrypted two-way communications session.
Self Assessment
Fill in the blanks:
7. Digital certificates are issued by a trusted third party known as a “...........................” .
8. Public key encryption uses ...........................to encrypt all data between the customer’s
computer and the e-commerce website. Information is sent in encrypted form to the site
using the site’s public key.
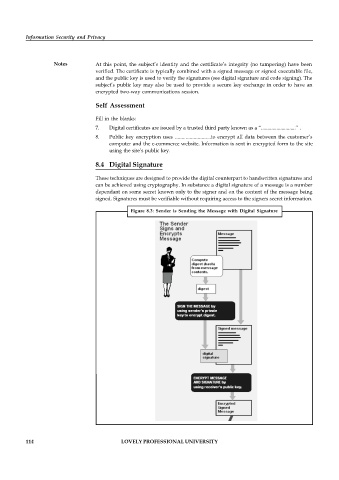
8.4 Digital Signature
These techniques are designed to provide the digital counterpart to handwritten signatures and
can be achieved using cryptography. In substance a digital signature of a message is a number
dependant on some secret known only to the signer and on the content of the message being
signed. Signatures must be verifiable without requiring access to the signers secret information.
Figure 8.3: Sender is Sending the Message with Digital Signature
114 LOVELY PROFESSIONAL UNIVERSITY