Page 27 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 27
Unit 2: Threats
Notes
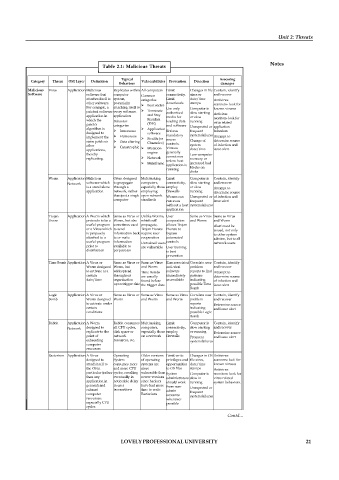
Table 2.1: Malicious Threats
Typical Assessing
Category Threat OSI Layer Definition Vulnerabilities Prevention Detection
Behaviors damages
Malicious Virus Application Malicious Replicates within All computers Limit Changes in file Contain, identify
Software software that computer Common connectivity. sizes or and recover
attaches itself to system, categories Limit date/time Antivirus
other software. potentially Boot sector downloads stamps scanners- look for
For example, a attaching itself to Use only Computer is known viruses
patched software every software Terminate authorized slow starting Antivirus
application in application and Stay media for or slow
which the Behavior Resident loading data running monitors- look for
virus related
patch’s categories (TSR) and software
algorithm is Innocuous Application Enforce Unexpected or application
frequent
behaviors
designed to software system failures
implement the Humorous mandatory Attempt to
Stealth (or access
same patch on Data altering Change of determine source
Chameleo) controls.
other system of infection and
Catastrophic Mutation Viruses
applications, date/time issue alert
thereby engine generally Low computer
replicating. Network cannot run memory or
unless host
Mainframe increased bad
application is
running blocks on
disks
Worm Application Malicious Often designed Multitasking Limit Computer is Contain, identify
Network software which to propagate computers, connectivity, slow starting and recover
is a stand alone through a especially those employ or slow Attempt to
application network, rather employing firewalls running determine source
than just a single open network Worms can Unexpected or of infection and
computer standards run even frequent issue alert
without a host system failures
application
Trojan Application A Worm which Same as Virus or Unlike Worms, User Same as Virus Same as Virus
Horse pretends to be a Worm, but also which self cooperation and Worm and Worm
useful program sometimes used propagate, allows Trojan Alert must be
or a Virus which to send Trojan Horses Horses to issued, not only
is purposely information back require user bypass to other system
attached to a to or make cooperation automated admins, but to all
useful program information Untrained users controls network users
prior to available to are vulnerable User training
distribution perpetrator is best
prevention
Time Bomb Application A Virus or Same as Virus or Same as Virus Run associated Correlate user Contain, identify
Worm designed Worm, but and Worm anti-viral problem and recover
to activate at a widespread Time Bombs software reports to find Attempt to
certain throughout are usually immediately patterns determine source
date/time organization found before as available indicating of infection and
upon trigger date the trigger date possible Time issue alert
Bomb
Logic Application A Virus or Same as Virus or Same as Virus Same as Virus Correlate user Contain, identify
Bomb Worm designed Worm and Worm and Worm problem and recover
to activate under reports Determine source
certain indicating and issue alert
conditions possible Logic
Bomb
Rabbit Application A Worm Rabbit consumes Multitasking Limit Computer is Contain, identify
Network designed to all CPU cycles, computers, connectivity, slow starting and recover
replicate to the disk space or especially those employ or running Determine source
point of network on a network firewalls Frequent and issue alert
exhausting resources, etc. system failures
computer
resources
Bacterium Application A Virus Operating Older versions Limit write Changes in OS Antivirus
designed to System of operating privileges and file sizes, scanners: look for
attach itself to consumes more systems are opportunities date/time known viruses
the OS in and more CPU more to OS files stamps Antivirus
particular (rather cycles, resulting vulnerable than System Computer is monitors: look for
than any eventually in newer versions administrators slow in virus related
application in noticeable delay since hackers should work running system behaviors.
general) and in user have had more from non- Unexpected or
exhaust transactions time to write admin
computer Bacterium accounts frequent
system failures
resources, whenever
especially CPU possible
cycles
Spoofing Spoofing Network Getting one Spoofing Automation Limit system Monitor Disconnect
Contd...
Data Link computer on a computer often services privileges of transaction automation
network to doesn’t have designed for automation logs of services until
pretend to have access to user network services to automation patched or
the identity of level commands interoperability minimum services, monitor
another so attempts to are especially necessary scanning for automation
computer, use automation vulnerable, Upgrade via unusual access points,
LOVELY PROFESSIONAL UNIVERSITY
usually one with level services, especially those such as network 21