Page 30 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 30
Information Security and Privacy
Notes
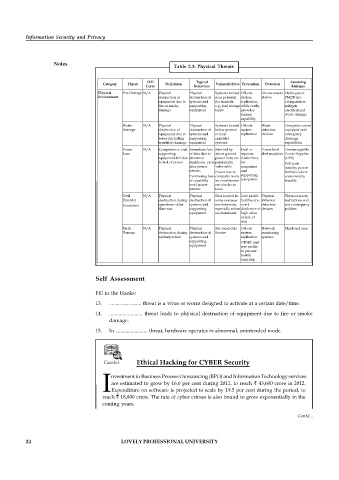
Table 2.3: Physical Threats
OSI Typical Assessing
Category Threat Definition Vulnerabilities Prevention Detection
Layer Behaviors damages
Physical Fire Damage N/A Physical Physical Systems located Off-site On-site smoke Halon gas or
Environment destruction of destruction of near potential system alarms FM200 fire
equipment due to systems and fire hazards, replication, extinguishers
fire or smoke supporting e.g., fuel storage while costly, mitigate
damage equipment tanks provides electrical and
backup water damage
capability
Water N/A Physical Physical Systems located Off-site Water Computer rooms
Damage destruction of destruction of below ground system detection equipped with
equipment due to systems and or near replication devices emergency
water (including supporting sprinkler drainage
sprinkler) damage equipment systems capabilities
Power N/A Computers or vital Immediate loss Sites fed by Dual or Power level Uninterruptible
Loss supporting of data due to above ground separate alert monitors Power Supplies
equipment fail due abnormal power lines are feeder lines (UPS)
to lack of power shutdown, even particularly for Full scale
after power vulnerable computers standby power
returns and
Power loss to facilities where
Continuing loss computer room supporting economically
of capability air conditioners equipment feasible
until power can also be an
returns issue
Civil N/A Physical Physical Sites located in Low profile Physical Physical access
Disorder destruction during destruction of some overseas facilities (no intrusion restrictions and
Vandalism operations other systems and environments, overt detection riot contingency
than war supporting especially urban disclosure of devices policies
equipment environments high value
nature of
site)
Battle N/A Physical Physical Site located in Off-site Network Hardened sites
Damage destruction during destruction of theater system monitoring
military action systems and replication systems
supporting OPSEC and
equipment low profile
to prevent
hostile
targeting
Self Assessment
Fill in the blanks:
13. ......................... threat is a virus or worm designed to activate at a certain date/time.
14. ......................... threat leads to physical destruction of equipment due to fire or smoke
damage.
15. In ......................... threat, hardware operates in abnormal, unintended mode.
Caselet Ethical Hacking for CYBER Security
nvestment in Business Process Outsourcing (BPO) and Information Technology services
are estimated to grow by 16.6 per cent during 2011, to reach 43,600 crore in 2012.
IExpenditure on software is projected to scale by 19.5 per cent during the period, to
reach 18,800 crore. The rate of cyber crimes is also bound to grow exponentially in the
coming years.
Contd...
24 LOVELY PROFESSIONAL UNIVERSITY