Page 64 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 64
Information Security and Privacy
Notes Civil Unrest
Electronic system might be popular targets for attack by politically motivated groups and
individuals as well as by mobs. It is undesirable that an electronic system site should be in
vicinity with:
1. Unusually high risk of mob violence,
2. Unusually high incidence of criminal and malicious damage,
3. Unusually high risk terrorist activity.
If such a site is unavoidable, additional levels of physical security may be appropriate.
Computer Terrorism
Computer terrorism is the act of destroying or of corrupting computer systems with an aim of
destabilizing a country or of applying pressure on a government. It is the act of doing something
intended to destabilize a country or to apply pressure on a government by using methods
classified in the category of computer crimes.
It is possible to carry out three types of actions against an information system, a physical,
syntactic attack and semantic attack:
1. The physical attack consists of damaging equipment in a “traditional” way, bomb, fire,
etc.
2. The syntactic attack consists of modifying the logic of the system in order to introduce
delays or to make the system unpredictable. An attack by means of a virus or of a Trojan
horse is included in this category.
3. The semantic attack is more perfidious. It exploits the confidence that the users have in
their system. It consist of modifying information that is entering or exiting the system,
without the users’ knowledge, in order to induce errors.
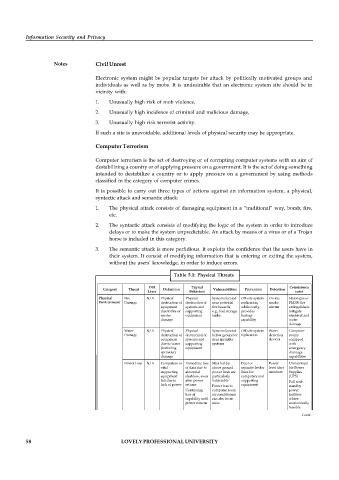
Table 5.1: Physical Threats
OSI Typical Countermea
Category Threat Definition Vulnerabilities Prevention Detection
Layer Behaviors sures
Physical Fire N/A Physical Physical Systems located Off-site system On-site Halon gas or
Environment Damage destruction of destruction of near potential replication, smoke FM200 fire
equipment systems and fire hazards, while costly, alarms extinguishers
due to fire or supporting e.g., fuel storage provides mitigate
smoke equipment tanks backup electrical and
damage capability water
damage
Water N/A Physical Physical Systems located Off-site system Water Computer
Damage destruction of destruction of below ground or replication detection rooms
equipment systems and near sprinkler devices equipped
due to water supporting systems with
(including equipment emergency
sprinkler) drainage
damage capabilities
Power Loss N/A Computers or Immediate loss Sites fed by Dual or Power Uninterrupti
vital of data due to above ground separate feeder level alert ble Power
supporting abnormal power lines are lines for monitors Supplies
equipment shutdow, even particularly computers and (UPS)
fail due to after power vulnerable supporting Full scale
lack of power returns equipment
Power loss to standby
Continuing computer room power
loss of air conditioners facilities
capability until can also be an where
power returns issue economically
feasible
Civil N/A Physical Physical Sites located in Low profile Physical Physical Contd...
Disorder destruction destruction of some overseas facilities (no intrusion access
Vandalism during systems and environments, overt disclosure detection restrictions
operations supporting especially urban of high value devices and riot
other than equipment environments nature of site) contingency
war policies
58 LOVELY PROFESSIONAL UNIVERSITY Off-site system Network Hardened
Battle
Site located in
Physical
Physical
N/A
Damage destruction destruction of theater replication monitorin sites
during systems and OPSEC and low g systems
military supporting profile to
action equipment
prevent hostile
targeting