Page 67 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 67
Unit 5: Physical Security
An IDS can be composed of several components: Sensors which generate security events, a Notes
Console to monitor events and alerts and control the sensors, and a central Engine that records
events logged by the sensors in a database and uses a system of rules to generate alerts from
security events received.
!
Caution In many simple IDS implementations all three components are combined in a
single device or appliance.
There are several ways to categorize an IDS depending on the type and location of the sensors
and the methodology used by the engine to generate alerts. While there are several types of
IDSs, the most common types work the same. They analyze network traffic and log files for
certain patterns. What kind of patterns you may ask? While a firewall will continually block a
hacker from connecting to a network, most firewalls never alert an administrator.
The administrator may notice if he/she checks the access log of the firewall, but that could be
weeks or even months after the attack. This is where an IDS comes into play. The attempts to pass
through the firewall are logged, and IDS will analyze its log. At some point in the log there will
be a large number of request-reject entries.
An IDS will flag the events and alert an administrator. The administrator can then see what is
happening right after or even while the attacks are still taking place. This gives an administrator
the advantage of being able to analyze the techniques being used, source of attacks, and methods
used by the hacker.
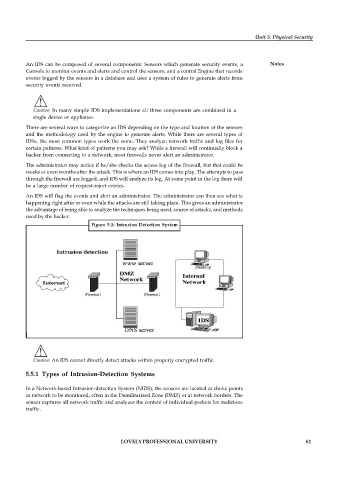
Figure 5.1: Intrusion Detection System
!
Caution An IDS cannot directly detect attacks within properly encrypted traffic.
5.5.1 Types of Intrusion-Detection Systems
In a Network-based Intrusion-detection System (NIDS), the sensors are located at choke points
in network to be monitored, often in the Demilitarized Zone (DMZ) or at network borders. The
sensor captures all network traffic and analyzes the content of individual packets for malicious
traffic.
LOVELY PROFESSIONAL UNIVERSITY 61