Page 70 - DCAP104_EXPOSURE_TO_COMPUTER_DISCPLINES
P. 70
Unit 4: Introduction of Networks
Although this solution is workable on small networks, it introduces the possibility that users may Notes
have to know and remember the passwords assigned to every resource, and then re-learn them
if the user of a particular machine decides to change them! Due to this flexibility and individual
discretion, institutionalised chaos is the norm for peer-to-peer networks.
Security can also be a major concern, because users may give passwords to other unauthorised
users, allowing them to access areas of the network that the company does not permit. Furthermore,
due to lack of centralisation, it is impossible for users to know and remember what data lives on
what machine, and there are no restrictions to prevent them from over-writing the wrong files
with older versions of the file. This of course cripples attempts to organise proper backups.
It may appear that peer-to-peer networks are hardly worthwhile. However, they offer some
powerful incentives, particularly for smaller organisations. Networks of this type are the cheapest
and easiest to install, requiring only Windows95, a network card for each machine and some
cabling. Once connected, users can start to share information immediately and get access to devices.
As a result, networks of this type are not scalable and a limit of no more than 10 machines is the
general rule.
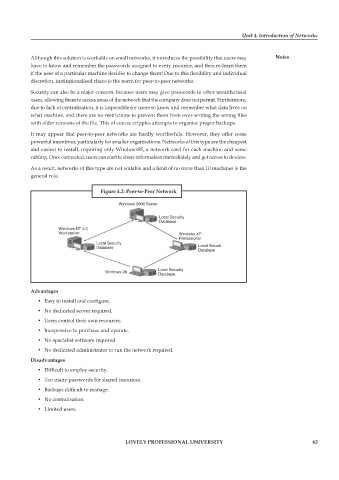
Figure 4.2: Peer-to-Peer Network
Windows 2000 Server
Local Security
Database
Windows NT 4.0
Workstation Windows XP
Professional
Local Security
Database Local Security
Database
Local Security
Windows 98
Database
Advantages
• Easy to install and configure.
• No dedicated server required.
• Users control their own resources.
• Inexpensive to purchase and operate.
• No specialist software required.
• No dedicated administrator to run the network required.
Disadvantages
• Difficult to employ security.
• Too many passwords for shared resources.
• Backups difficult to manage.
• No centralisation.
• Limited users.
LOVELY PROFESSIONAL UNIVERSITY 63