Page 167 - DCAP103_Principle of operating system
P. 167
Principles of Operating Systems
Notes 5.5.3 Protection
Memory protection in a paged environment is accomplished by protection bits 11 that are
associated with each frame. Normally, these bits are kept in the page table. One bit can define
a page to be read-write or read-only. Every reference to memory goes through the page table to
find the correct frame number. At the same time that the physical address is being computed,
the protection bits can be checked to verify that no writes are being made to a read-only page.
An attempt to write to a read-only page causes a hardware trap to the operating system (or
memory-protection violation). We can easily expand this approach to provide a finer level of
protection. We can create hardware to provide read-only, read-write, or execute-only protection.
Or, by providing separate protection bits for each kind of access, we can allow any combination
of these accesses; illegal attempts will be trapped to the operating system. One more bit is
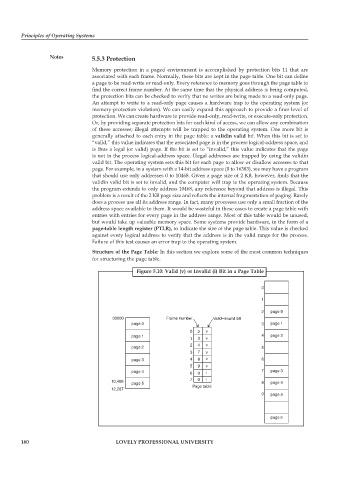
generally attached to each entry in the page table: a validin valid bit. When this bit is set to
“valid,” this value indicates that the associated page is in the process logical-address space, and
is thus a legal (or valid) page. If the bit is set to “invalid,” this value indicates that the page
is not in the process logical-address space. Illegal addresses are trapped by using the validin
valid bit. The operating system sets this bit for each page to allow or disallow accesses to that
page. For example, in a system with a 14-bit address space (0 to 16383), we may have a program
that should use only addresses 0 to 10468. Given a page size of 2 KB, however, finds that the
validin valid bit is set to invalid, and the computer will trap to the operating system. Because
the program extends to only address 10468, any reference beyond that address is illegal. This
problem is a result of the 2 KB page size and reflects the internal fragmentation of paging. Rarely
does a process use all its address range. In fact, many processes use only a small fraction of the
address space available to them. It would be wasteful in these cases to create a page table with
entries with entries for every page in the address range. Most of this table would be unused,
but would take up valuable memory space. Some systems provide hardware, in the form of a
page-table length register (PTLR), to indicate the size of the page table. This value is checked
against every logical address to verify that the address is in the valid range for the process.
Failure of this test causes an error trap to the operating system.
Structure of the Page Table: In this section we explore some of the most common techniques
for structuring the page table.
Figure 5.10: Valid (v) or Invalid (i) Bit in a Page Table
160 LOVELY PROFESSIONAL UNIVERSITY