Page 166 - DCAP103_Principle of operating system
P. 166
Unit 5: Memory Management
Furthermore, some TLBs allow entries to be wired down, meaning that they cannot be removed Notes
from the TLB. Typically, TLB entries for kernel code are often wired down. Some TLBs store
address-space identifiers (ASIDs) in each entry of the TLB. An ASID uniquely identifies each
process and is used to provide address space protection for that process. When the TLB attempts
to resolve virtual page numbers, it ensures the ASID for the currently running process matches
the ASID associated with the virtual page. If the ASIDs do not match, they are treated as a TLB
miss. In addition to providing address-space protection, an ASID allows the TLB to contain
entries for several different processes simultaneously.
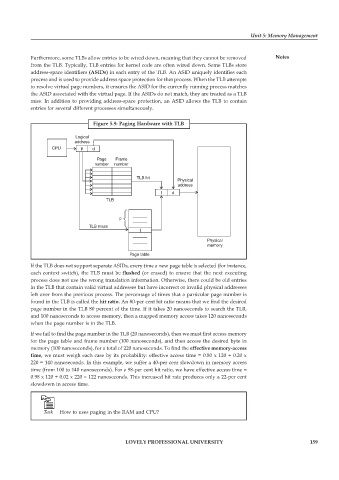
Figure 5.9: Paging Hardware with TLB
If the TLB does not support separate ASIDs, every time a new page table is selected (for instance,
each context switch), the TLB must be flushed (or erased) to ensure that the next executing
process does not use the wrong translation information. Otherwise, there could be old entries
in the TLB that contain valid virtual addresses but have incorrect or invalid physical addresses
left over from the previous process. The percentage of times that a particular page number is
found in the TLB is called the hit ratio. An 80-per cent hit ratio means that we find the desired
page number in the TLB 80 percent of the time. If it takes 20 nanoseconds to search the TLB,
and 100 nanoseconds to access memory, then a mapped memory access takes 120 nanoseconds
when the page number is in the TLB.
If we fail to find the page number in the TLB (20 nanoseconds), then we must first access memory
for the page table and frame number (100 nanoseconds), and then access the desired byte in
memory (100 nanoseconds), for a total of 220 nanoseconds. To find the effective memory-access
time, we must weigh each case by its probability: effective access time = 0.80 x 120 + 0.20 x
220 = 140 nanoseconds. In this example, we suffer a 40-per cent slowdown in memory access
time (from 100 to 140 nanoseconds). For a 98-per cent hit ratio, we have effective access time =
0.98 x 120 + 0.02 x 220 = 122 nanoseconds. This increased hit rate produces only a 22-per cent
slowdown in access time.
How to uses paging in the RAM and CPU?
LOVELY PROFESSIONAL UNIVERSITY 159