Page 244 - DCAP312_WEB_TECHNOLOGIES_II
P. 244
Web Technologies-II
Notes In addition to the built-in ASP.NET features, an ASP.NET application can use the low-level
security features of the .NET Framework. For more information, see the “Key Security Concepts”
topic in .NET Framework Help.
The Security Data Flow
There are a number of different ways to design security into ASP.NET applications. This is
describes the data flow for two common scenarios: impersonation and forms authentication
using cookies.
Scenario 1: Impersonation
This scenario relies on Internet Information Services (IIS) authentication and Microsoft Windows
NT file access security to minimize security programming in the ASP.NET application itself.
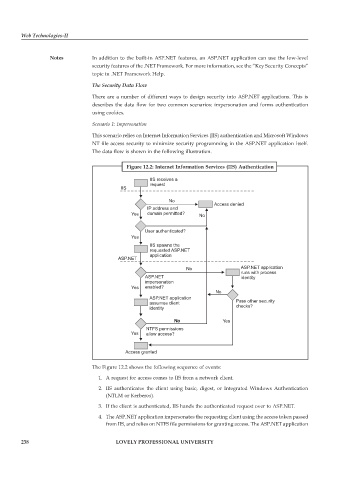
The data flow is shown in the following illustration.
Figure 12.2: Internet Information Services (IIS) Authentication
IIS receives a
request
IIS
No
Access denied
IP address and
Yes domain permitted? No
User authenticated?
Yes
IIS spawns the
requested ASP.NET
application
ASP.NET
No ASP.NET application
runs with process
ASP.NET identity
impersonation
Yes enabled?
No
ASP.NET application
assumes client Pass other security
identity checks?
No Yes
No
NTFS permissions
Yes allow access?
Access granted
The Figure 12.2 shows the following sequence of events:
1. A request for access comes to IIS from a network client.
2. IIS authenticates the client using basic, digest, or Integrated Windows Authentication
(NTLM or Kerberos).
3. If the client is authenticated, IIS hands the authenticated request over to ASP.NET.
4. The ASP.NET application impersonates the requesting client using the access token passed
from IIS, and relies on NTFS file permissions for granting access. The ASP.NET application
238 LOVELY PROFESSIONAL UNIVERSITY