Page 221 - DCAP403_Operating System
P. 221
Operating System
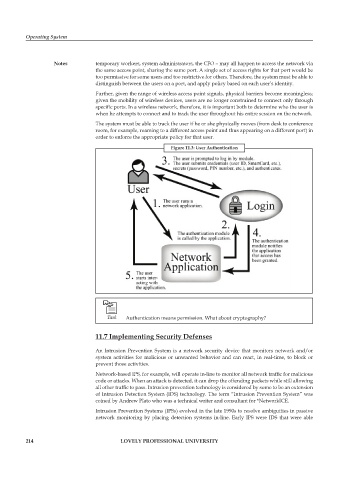
Notes temporary workers, system administrators, the CFO – may all happen to access the network via
the same access point, sharing the same port. A single set of access rights for that port would be
too permissive for some users and too restrictive for others. Therefore, the system must be able to
distinguish between the users on a port, and apply policy based on each user’s identity.
Further, given the range of wireless access point signals, physical barriers become meaningless;
given the mobility of wireless devices, users are no longer constrained to connect only through
specific ports. In a wireless network, therefore, it is important both to determine who the user is
when he attempts to connect and to track the user throughout his entire session on the network.
The system must be able to track the user if he or she physically moves (from desk to conference
room, for example, roaming to a different access point and thus appearing on a different port) in
order to enforce the appropriate policy for that user.
Figure 11.3: User Authentication
Task Authentication means permission. What about cryptography?
11.7 Implementing Security Defenses
An Intrusion Prevention System is a network security device that monitors network and/or
system activities for malicious or unwanted behavior and can react, in real-time, to block or
prevent those activities.
Network-based IPS, for example, will operate in-line to monitor all network traffic for malicious
code or attacks. When an attack is detected, it can drop the offending packets while still allowing
all other traffic to pass. Intrusion prevention technology is considered by some to be an extension
of Intrusion Detection System (IDS) technology. The term “Intrusion Prevention System” was
coined by Andrew Plato who was a technical writer and consultant for *NetworkICE.
Intrusion Prevention Systems (IPSs) evolved in the late 1990s to resolve ambiguities in passive
network monitoring by placing detection systems in-line. Early IPS were IDS that were able
214 LOVELY PROFESSIONAL UNIVERSITY