Page 218 - DCAP403_Operating System
P. 218
Unit 11: System Security
There are several tools of cryptography and these are: Notes
11.5.1 Hashing
Hash functions, also called message digests and one-way encryption, are algorithms that, in some
sense, use no key. Instead, a fixed-length hash value is computed based upon the plaintext that
makes it impossible for either the contents or length of the plaintext to be recovered.
Hash algorithms are typically used to provide a digital fingerprint of a fi le’s contents, often
used to ensure that the file has not been altered by an intruder or virus. Hash functions are also
commonly employed by many operating systems to encrypt passwords. Hash functions, then,
provide a measure of the integrity of a fi le.
Broadly speaking, a cryptographic hash function should behave as much as possible like a
random function while still being deterministic and effi ciently computable.
A cryptographic hash function is considered insecure if either of the following is computationally
feasible:
1. Finding a (previously unseen) message that matches a given digest.
2. Finding “collisions”, wherein two different messages have the same message digest.
An attacker who can do either of these things might, for example, use them to substitute an
unauthorized message for an authorized one.
Ideally, it should not even be feasible to find two messages whose digests are substantially similar;
nor would one want an attacker to be able to learn anything useful about a message given only its
digest. Of course the attacker learns at least one piece of information, the digest itself, which for
instance gives the attacker the ability to recognise the same message should it occur again.
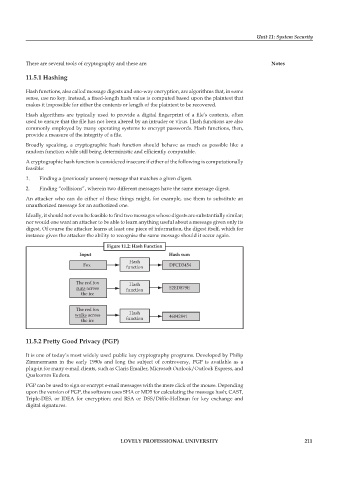
Figure 11.2: Hash Function
Input Hash sum
Hash
Fox DFCD3454
function
The red fox Hash
runs across function 52ED879E
the ice
The red fox
walks across Hash 46042841
the ice function
11.5.2 Pretty Good Privacy (PGP)
It is one of today’s most widely used public key cryptography programs. Developed by Philip
Zimmermann in the early 1990s and long the subject of controversy, PGP is available as a
plug-in for many e-mail clients, such as Claris Emailer, Microsoft Outlook/Outlook Express, and
Qualcomm Eudora.
PGP can be used to sign or encrypt e-mail messages with the mere click of the mouse. Depending
upon the version of PGP, the software uses SHA or MD5 for calculating the message hash; CAST,
Triple-DES, or IDEA for encryption; and RSA or DSS/Diffie-Hellman for key exchange and
digital signatures.
LOVELY PROFESSIONAL UNIVERSITY 211