Page 214 - DCAP403_Operating System
P. 214
Unit 11: System Security
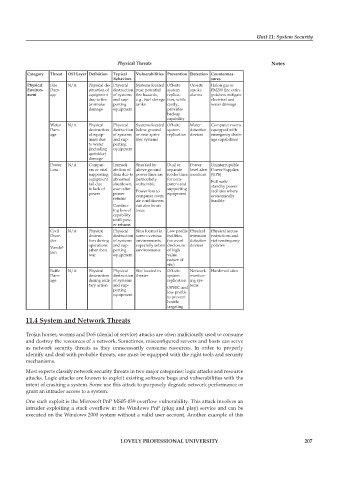
Physical Threats Notes
Category Threat OSI Layer Defi nition Typical Vulnerabilities Prevention Detection Countermea-
Behaviors sures
Physical Fire N/A Physical de- Physical Systems located Off-site On-site Halon gas or
Environ- Dam- struction of destruction near potential system smoke FM200 fi re extin-
ment age equipment of systems fi re hazards, replica- alarms guishers mitigate
due to fi re and sup- e.g., fuel storage tion, while electrical and
or smoke porting tanks costly, water damage
damage equipment provides
backup
capability
Water N/A Physical Physical Systems located Off-site Water Computer rooms
Dam- destruction destruction below ground system detection equipped with
age of equip- of systems or near sprin- replication devices emergency drain-
ment due and sup- kler systems age capabilities
to water porting
(including equipment
sprinkler)
damage
Power N/A Comput- Immedi- Sites fed by Dual or Power Uninterruptible
Loss ers or vital ate loss of above ground separate level alert Power Supplies
supporting data due to power lines are feeder lines monitors (UPS)
equipment abnormal particularly for com- Full scale
fail due shutdown, vulnerable puters and standby power
to lack of even after Power loss to supporting facilities where
power power computer room equipment economically
returns
air conditioners feasible
Continu- can also be an
ing loss of issue
capability
until pow-
er returns
Civil N/A Physical Physical Sites located in Low profi le Physical Physical access
Disor- destruc- destruction some overseas facilities intrusion restrictions and
der tion during of systems environments, (no overt detection riot contingency
operations and sup- especially urban disclosure devices policies
Vandal-
ism other than porting environments of high
war equipment value
nature of
site)
Battle N/A Physical Physical Site located in Off-site Network Hardened sites
Dam- destruction destruction theater system monitor-
age during mili- of systems replication ing sys-
tary action and sup- OPSEC and tems
porting low profi le
equipment
to prevent
hostile
targeting
11.4 System and Network Threats
Trojan horses, worms and DoS (denial of service) attacks are often maliciously used to consume
and destroy the resources of a network. Sometimes, misconfi gured servers and hosts can serve
as network security threats as they unnecessarily consume resources. In order to properly
identify and deal with probable threats, one must be equipped with the right tools and security
mechanisms.
Most experts classify network security threats in two major categories: logic attacks and resource
attacks. Logic attacks are known to exploit existing software bugs and vulnerabilities with the
intent of crashing a system. Some use this attack to purposely degrade network performance or
grant an intruder access to a system.
One such exploit is the Microsoft PnP MS05-039 overflow vulnerability. This attack involves an
intruder exploiting a stack overflow in the Windows PnP (plug and play) service and can be
executed on the Windows 2000 system without a valid user account. Another example of this
LOVELY PROFESSIONAL UNIVERSITY 207