Page 211 - DCAP403_Operating System
P. 211
Operating System
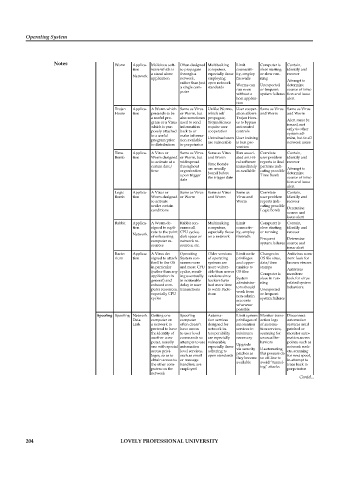
Notes Worm Applica- Malicious soft- Often designed Multitasking Limit Computer is Contain,
tion ware which is to propagate computers, connectiv- slow starting identify and
a stand alone through a especially those ity, employ or slow run- recover
Network
application network, employing firewalls ning
rather than just open network Worms can Unexpected Attempt to
determine
a single com- standards run even or frequent source of infec-
puter
without a system failures tion and issue
host applica- alert
tion
Trojan Applica- A Worm which Same as Virus Unlike Worms, User cooper- Same as Virus Same as Virus
Horse tion pretends to be or Worm, but which self ation allows and Worm and Worm
a useful pro- also sometimes propagate, Trojan Hors- Alert must be
gram or a Virus used to send Trojan Horses es to bypass
issued, not
which is pur- information require user automated
posely attached back to or cooperation controls only to other
system ad-
to a useful make informa- Untrained users User training mins, but to all
program prior tion available are vulnerable is best pre- network users
to distribution to perpetrator
vention
Time Applica- A Virus or Same as Virus Same as Virus Run associ- Correlate Contain,
Bomb tion Worm designed or Worm, but and Worm ated anti-vi- user problem identify and
to activate at a widespread Time Bombs ral software reports to find recover
certain date/ throughout are usually immediately patterns indi- Attempt to
time organization as available cating possible
found before determine
upon trigger the trigger date Time Bomb source of infec-
date
tion and issue
alert
Logic Applica- A Virus or Same as Virus Same as Virus Same as Correlate Contain,
Bomb tion Worm designed or Worm and Worm Virus and user problem identify and
to activate Worm reports indi- recover
under certain cating possible Determine
conditions Logic Bomb
source and
issue alert
Rabbit Applica- A Worm de- Rabbit con- Multitasking Limit Computer is Contain,
tion signed to repli- sumes all computers, connectiv- slow starting identify and
cate to the point CPU cycles, especially those ity, employ or running recover
Network
of exhausting disk space or on a network firewalls Frequent Determine
computer re- network re-
system failures source and
sources sources, etc.
issue alert
Bacte- Applica- A Virus de- Operating Older versions Limit write Changes in Antivirus scan-
rium tion signed to attach System con- of operating privileges OS file sizes, ners: look for
itself to the OS sumes more systems are and oppor- date/time known viruses
in particular and more CPU more vulner- tunities to stamps
(rather than any cycles, result- able than newer OS files Computer is Antivirus
monitors:
application in ing eventually versions since System slow in run- look for virus
general) and in noticeable hackers have administra- ning related system
exhaust com- delay in user had more time tors should behaviors.
puter resources, transactions to write Bacte- Unexpected
especially CPU rium work from or frequent
non-admin
cycles system failures
accounts
whenever
possible
Spoofing Spoofing Network Getting one Spoofing Automa- Limit system Monitor trans- Disconnect
Data computer on computer tion services privileges of action logs automation
Link a network to often doesn’t designed for automation of automa- services until
pretend to have have access network in- services to tion services, patched or
the identity of to user level teroperability minimum scanning for monitor auto-
another com- commands so are especially necessary unusual be- mation access
puter, usually attempts to use vulnerable, Upgrade haviors points, such as
one with special automation especially those via security If automating network sock-
access privi- level services, adhering to patches as this process do ets, scanning
leges, so as to such as email open standards for next spoof,
they become so off-line to
obtain access to or message in attempt to
the other com- handlers, are available avoid “tunnel- trace back to
ing” attacks
puters on the employed perpetrator
network
Contd...
204 LOVELY PROFESSIONAL UNIVERSITY