Page 213 - DCAP403_Operating System
P. 213
Operating System
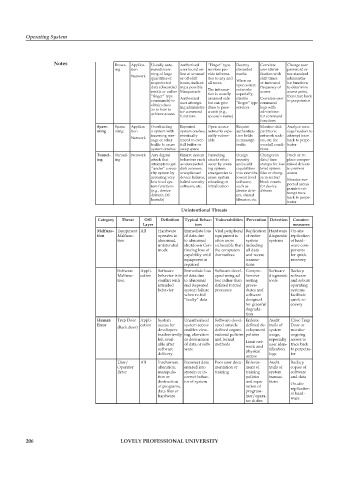
Notes Brows- Applica- Usually auto- Authorized “Finger” type Destroy Correlate Change user
ing tion mated scan- user found on- services pro- discarded user identi- password or
ning of large line at unusual vide informa- media fi cation with use standard
Network quantities of or off-shift tion to any and shift times administra-
unprotected hours, indicat- all users. When on or increased tor functions
open source
data (discarded ing a possible The informa- networks frequency of to determine
media or online Masquerade tion is usually especially, access access point,
“fi nger” type then trace back
commands) to Authorized assumed safe disable Correlate user to perpetrator
user attempt-
“fi nger” type command
but can give
obtain clues ing administra- clues to pass- services logs with
as to how to tor command words (e.g., administra-
achieve access
functions spouse’s name) tor command
functions
Spam- Spam- Applica- Overloading Repeated Open source Require Monitor disk Analyze mes-
ming ming tion a system with system crashes, networks espe- authentica- partitions, sage headers to
incoming mes- eventually cially vulner- tion fi elds network sock- attempt trace
Network
sage or other traced to over- able in message ets, etc. for back to perpe-
traffic to cause full buffer or traffi c overfull condi- trator
system crashes swap space tions
Tunnel- Tunnel- Network Any digital Bizarre system Tunneling Design Changes in Patch or re-
ing ing attack that behaviors such attacks often security date/time place compro-
attempts to get as unexpected occur by creat- and audit stamps for low mised drivers
“under” a secu- disk accesses, ing system capabilities level system to prevent
rity system by unexplained emergencies to into even the fi les or chang- access
accessing very device failures, cause system lowest level es in sector/ Monitor sus-
low level sys- halted security reloading or software, block counts pected access
tem functions software, etc. initialization such as for device
(e.g., device device driv- drivers points to at-
tempt trace
drivers, OS ers, shared back to perpe-
kernels) libraries, etc.
trator
Unintentional Threats
Category Threat OSI Defi nition Typical Behav- Vulnerabilities Prevention Detection Counter-
Layer iors measures
Malfunc- Equipment All Hardware Immediate loss Vital peripheral Replication Hardware On-site
tion Malfunc- operates in of data due equipment is of entire diagnostic replication
tion abnormal, to abnormal often more system systems of hard-
unintended shutdown Con- vulnerable than including ware com-
mode tinuing loss of the computers all data ponents
capability until themselves and recent for quick
equipment is transac- recovery
repaired tions
Software Appli- Software Immediate loss Software devel- Compre- Software Backup
Malfunc- cation behavior is in of data due oped using ad hensive diagnostic software
tion confl ict with to abnormal hoc rather than testing tools and robust
intended end Repeated defi ned formal proce- operating
behavior system failure processes dures and systems
when re-fed software facilitate
“faulty” data designed quick re-
for graceful covery
degrada-
tion
Human Trap Door Appli- System Unauthorized Software devel- Enforce Audit Close Trap
Error cation access for system access oped outside defi ned de- trails of Door or
(Back door)
developers enables view- defi ned organi- velopment system monitor
inadvertently ing, alteration zational policies policies usage, ongoing
left avail- or destruction and formal Limit net- especially access to
able after of data or soft- methods work and user iden- trace back
software ware physical tifi cation to perpetra-
delivery logs tor
access
User/ All Inadvertent Incorrect data Poor user docu- Enforce- Audit Backup
Operator alteration, entered into mentation or ment of trails of copies of
Error manipula- system or in- training training system software
tion or correct behav- policies transac- and data
destruction ior of system and sepa- tions On-site
of programs, ration of replication
data fi les or program- of hard-
hardware mer/opera- ware
tor duties
206 LOVELY PROFESSIONAL UNIVERSITY