Page 237 - DCAP403_Operating System
P. 237
Operating System
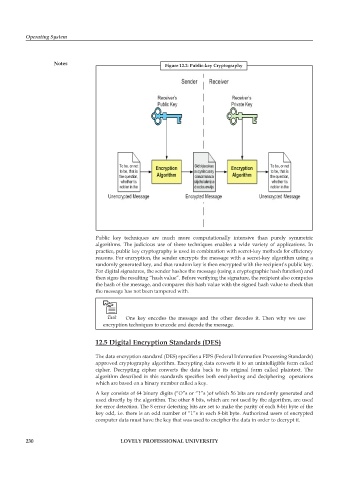
Notes Figure 12.2: Public-key Cryptography
Public key techniques are much more computationally intensive than purely symmetric
algorithms. The judicious use of these techniques enables a wide variety of applications. In
practice, public key cryptography is used in combination with secret-key methods for effi ciency
reasons. For encryption, the sender encrypts the message with a secret-key algorithm using a
randomly generated key, and that random key is then encrypted with the recipient’s public key.
For digital signatures, the sender hashes the message (using a cryptographic hash function) and
then signs the resulting “hash value”. Before verifying the signature, the recipient also computes
the hash of the message, and compares this hash value with the signed hash value to check that
the message has not been tampered with.
Task One key encodes the message and the other decodes it. Then why we use
encryption techniques to encode and decode the message.
12.5 Digital Encryption Standards (DES)
The data encryption standard (DES) specifies a FIPS (Federal Information Processing Standards)
approved cryptography algorithm. Encrypting data converts it to an unintelligible form called
cipher. Decrypting cipher converts the data back to its original form called plaintext. The
algorithm described in this standards specifies both enciphering and deciphering operations
which are based on a binary number called a key.
A key consists of 64 binary digits (“O”s or “1”s )of which 56 bits are randomly generated and
used directly by the algorithm. The other 8 bits, which are not used by the algorithm, are used
for error detection. The 8 error detecting bits are set to make the parity of each 8-bit byte of the
key odd, i.e. there is an odd number of “1”s in each 8-bit byte. Authorized users of encrypted
computer data must have the key that was used to encipher the data in order to decrypt it.
230 LOVELY PROFESSIONAL UNIVERSITY