Page 122 - DMGT505_MANAGEMENT_INFORMATION_SYSTEM
P. 122
Unit 6: Business Networks and Telecommunications
FTP session. It facilitates the exchange of commands issued by the client, and replies originating Notes
from server. Data connection is established as and when it is required. Its main function is to
facilitate transfer of files and directory listings to and from the client at the client’s request.
Whenever you wish to do FTP, you need to invoke a few commands. These commands basically
are related to transfer a file from remote computer to your computer or from your computer to
the remote computer. There are anonymous as well as authorized privileges with regard to
transfer of a file from a server. In case of anonymous FTP servers, you can do FTP without
authorization. You need to login with a user name, which is anonymous, and a password that is
your e-mail address. Apart from this, there are authorized servers for which you need to
register before you are permitted to do FTP. After registration, you will get a password.
UDP
The User Datagram Protocol enables application programs to have direct access to a datagram
delivery service like the delivery service that IP provides. This enables applications to exchange
messages over the network with a minimum of protocol overhead. UDP is connectionless
unreliable datagram protocol in which the sending terminal does not check whether data has
been received by receiving terminal. The unreliable service indicates that there is no guarantee
that the data reaches at the receiving end of the network correctly. It can be understood more
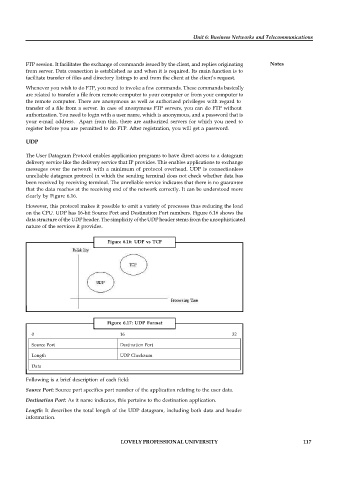
clearly by Figure 6.16.
However, this protocol makes it possible to omit a variety of processes thus reducing the load
on the CPU. UDP has 16-bit Source Port and Destination Port numbers. Figure 6.16 shows the
data structure of the UDP header. The simplicity of the UDP header stems from the unsophisticated
nature of the services it provides.
Figure 6.16: UDP vs TCP
Figure 6.17: UDP Format
0 16 32
Source Port Destination Port
Length UDP Checksum
Data
Following is a brief description of each field:
Source Port: Source port specifies port number of the application relating to the user data.
Destination Port: As it name indicates, this pertains to the destination application.
Length: It describes the total length of the UDP datagram, including both data and header
information.
LOVELY PROFESSIONAL UNIVERSITY 117