Page 105 - SOFTWARE TESTING & QUALITY ASSURANCE
P. 105
Software Testing and Quality Assurance
The following tasks are performed during this step.
(a) Identify what the system does and how it accesses the various subsystems.
In an employee database management system, the employee views various
subsystems such as financial data, personal data, and project data. The
managers view employee details, employee log in times, and so on.
(b) Create an architecture diagram of the system. The architecture diagram includes
subsystems, boundaries of operation, data flow channels, and so on.
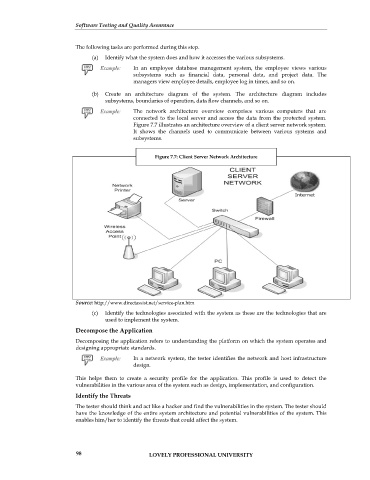
The network architecture overview comprises various computers that are
connected to the local server and access the data from the protected system.
Figure 7.7 illustrates an architecture overview of a client server network system.
It shows the channels used to communicate between various systems and
subsystems.
Figure 7.7: Client Server Network Architecture
Source: http://www.directassist.net/service-plan.htm
(c) Identify the technologies associated with the system as these are the technologies that are
used to implement the system.
Decompose the Application
Decomposing the application refers to understanding the platform on which the system operates and
designing appropriate standards.
In a network system, the tester identifies the network and host infrastructure
design.
This helps them to create a security profile for the application. This profile is used to detect the
vulnerabilities in the various area of the system such as design, implementation, and configuration.
Identify the Threats
The tester should think and act like a hacker and find the vulnerabilities in the system. The tester should
have the knowledge of the entire system architecture and potential vulnerabilities of the system. This
enables him/her to identify the threats that could affect the system.
98 LOVELY PROFESSIONAL UNIVERSITY