Page 104 - SOFTWARE TESTING & QUALITY ASSURANCE
P. 104
Unit 7: Documentation and Security Testing
Business requirements keep changing during the product development life cycle. The
developers have to make modifications to the actual specifications and design during
the product development. Carrying out the process of threat modeling regularly will
help in identifying the risks more efficiently and effectively and resolve them as soon
as possible.
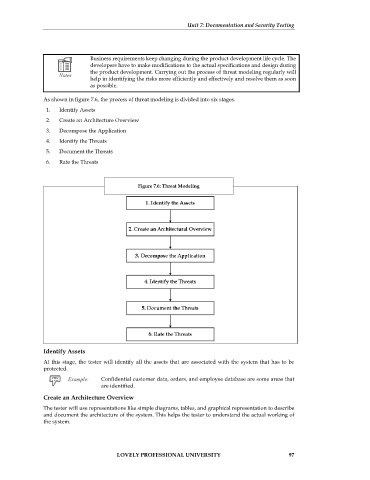
As shown in figure 7.6, the process of threat modeling is divided into six stages.
1. Identify Assets
2. Create an Architecture Overview
3. Decompose the Application
4. Identify the Threats
5. Document the Threats
6. Rate the Threats
Figure 7.6: Threat Modeling
Identify Assets
At this stage, the tester will identify all the assets that are associated with the system that has to be
protected.
Confidential customer data, orders, and employee database are some areas that
are identified.
Create an Architecture Overview
The tester will use representations like simple diagrams, tables, and graphical representation to describe
and document the architecture of the system. This helps the tester to understand the actual working of
the system.
LOVELY PROFESSIONAL UNIVERSITY 97