Page 239 - DCAP311_DCAP607_WIRELESS_NETWORKS
P. 239
Unit 14: Authentication
Notes
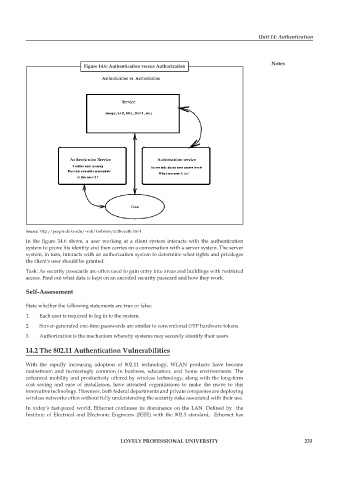
Figure 14.6: Authentication versus Authorization
Source: http://people.duke.edu/~rob/kerberos/authvauth.html
In the figure 14.6 above, a user working at a client system interacts with the authentication
system to prove his identity and then carries on a conversation with a server system. The server
system, in turn, interacts with an authorization system to determine what rights and privileges
the client's user should be granted.
Task: As security passcards are often used to gain entry into areas and buildings with restricted
access. Find out what data is kept on an encoded security passcard and how they work.
Self-Assessment
State whether the following statements are true or false:
1. Each user is required to log in to the system.
2. Server-generated one-time passwords are similar to conventional OTP hardware tokens.
3. Authorization is the mechanism whereby systems may securely identify their users.
14.2 The 802.11 Authentication Vulnerabilities
With the rapidly increasing adoption of 802.11 technology, WLAN products have become
mainstream and increasingly common in business, education, and home environments. The
enhanced mobility and productivity offered by wireless technology, along with the long-term
cost saving and ease of installation, have attracted organizations to make the move to this
innovative technology. However, both federal departments and private companies are deploying
wireless networks often without fully understanding the security risks associated with their use.
In today’s fast-paced world, Ethernet continues its dominance on the LAN. Defined by the
Institute of Electrical and Electronic Engineers (IEEE) with the 802.3 standard, Ethernet has
LOVELY PROFESSIONAL UNIVERSITY 233