Page 242 - DCAP311_DCAP607_WIRELESS_NETWORKS
P. 242
Wireless Networks
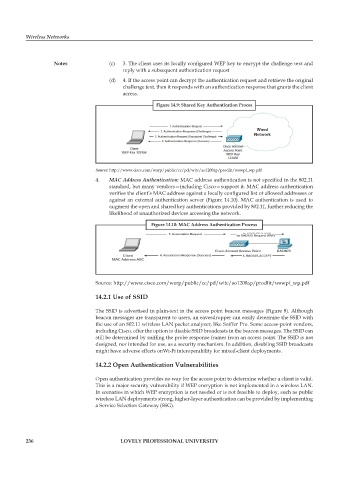
Notes (c) 3. The client uses its locally configured WEP key to encrypt the challenge text and
reply with a subsequent authentication request
(d) 4. If the access point can decrypt the authentication request and retrieve the original
challenge text, then it responds with an authentication response that grants the client
access.
Figure 14.9: Shared Key Authentication Proces
Source: http://www.cisco.com/warp/public/cc/pd/witc/ao1200ap/prodlit/wswpf_wp.pdf
4. MAC Address Authentication: MAC address authentication is not specified in the 802.11
standard, but many vendors—including Cisco—support it. MAC address authentication
verifies the client’s MAC address against a locally configured list of allowed addresses or
against an external authentication server (Figure 14.10). MAC authentication is used to
augment the open and shared key authentications provided by 802.11, further reducing the
likelihood of unauthorized devices accessing the network.
Figure 14.10: MAC Address Authentication Process
Source: http://www.cisco.com/warp/public/cc/pd/witc/ao1200ap/prodlit/wswpf_wp.pdf
14.2.1 Use of SSID
The SSID is advertised in plain-text in the access point beacon messages (Figure 8). Although
beacon messages are transparent to users, an eavesdropper can easily determine the SSID with
the use of an 802.11 wireless LAN packet analyzer, like Sniffer Pro. Some access-point vendors,
including Cisco, offer the option to disable SSID broadcasts in the beacon messages. The SSID can
still be determined by sniffing the probe response frames from an access point. The SSID is not
designed, nor intended for use, as a security mechanism. In addition, disabling SSID broadcasts
might have adverse effects onWi-Fi interoperability for mixed-client deployments.
14.2.2 Open Authentication Vulnerabilities
Open authentication provides no way for the access point to determine whether a client is valid.
This is a major security vulnerability if WEP encryption is not implemented in a wireless LAN.
In scenarios in which WEP encryption is not needed or is not feasible to deploy, such as public
wireless LAN deployments strong, higher-layer authentication can be provided by implementing
a Service Selection Gateway (SSG).
236 LOVELY PROFESSIONAL UNIVERSITY