Page 243 - DCAP311_DCAP607_WIRELESS_NETWORKS
P. 243
Unit 14: Authentication
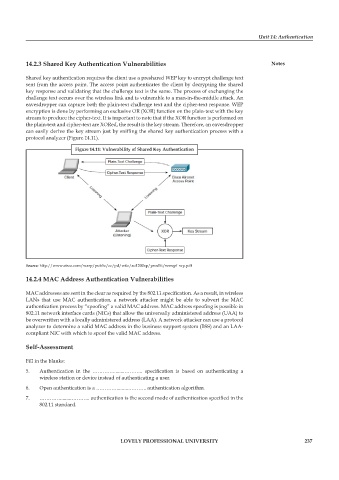
14.2.3 Shared Key Authentication Vulnerabilities Notes
Shared key authentication requires the client use a preshared WEP key to encrypt challenge text
sent from the access point. The access point authenticates the client by decrypting the shared
key response and validating that the challenge text is the same. The process of exchanging the
challenge text occurs over the wireless link and is vulnerable to a man-in-the-middle attack. An
eavesdropper can capture both the plain-text challenge text and the cipher-text response. WEP
encryption is done by performing an exclusive OR (XOR) function on the plain-text with the key
stream to produce the cipher-text. It is important to note that if the XOR function is performed on
the plain-text and cipher-text are XORed, the result is the key stream. Therefore, an eavesdropper
can easily derive the key stream just by sniffing the shared key authentication process with a
protocol analyzer (Figure 14.11).
Figure 14.11: Vulnerability of Shared Key Authentication
Source: http://www.cisco.com/warp/public/cc/pd/witc/ao1200ap/prodlit/wswpf_wp.pdf
14.2.4 MAC Address Authentication Vulnerabilities
MAC addresses are sent in the clear as required by the 802.11 specification. As a result, in wireless
LANs that use MAC authentication, a network attacker might be able to subvert the MAC
authentication process by “spoofing” a valid MAC address. MAC address spoofing is possible in
802.11 network interface cards (NICs) that allow the universally administered address (UAA) to
be overwritten with a locally administered address (LAA). A network attacker can use a protocol
analyzer to determine a valid MAC address in the business support system (BSS) and an LAA-
compliant NIC with which to spoof the valid MAC address.
Self-Assessment
Fill in the blanks:
5. Authentication in the ………….........……….. specification is based on authenticating a
wireless station or device instead of authenticating a user.
6. Open authentication is a ………….........……….. authentication algorithm.
7. ………….........……….. authentication is the second mode of authentication specified in the
802.11 standard.
LOVELY PROFESSIONAL UNIVERSITY 237