Page 174 - DCAP512_WAP_AND_WML
P. 174
WAP & WML
Notes Don’t try to restrict the wireless signal: Radio waves travel farther than you might realize, and
are almost impossible to limit or restrict. Don’t restrict the signal – it’s more effective and easier
to have the signal be as powerful as possible, but encrypt the data on it. If we can walk outside
your house and detect your wireless signal, no big deal: I’m still prevented from using it if
you’ve enabled the encryption methods specified above.
After you think you’ve gotten all PCs connected, reboot them and make sure they reconnect
automatically. Verify you can still connect to the network and/or Internet. This will ensure that
all changes are applied correctly and that those security changes will “stick”.
Self Assessment Questions
Fill in the blanks:
1. The ………………………. provides security for the data exchanged directly between the
wireless device and the WAP gateway.
2. All computers on a network must have a ………………………. address.
3. Use ………………………. for the authentication type and AES for the encryption method.
4. Like a computer’s fingerprint, all networked computers have a unique identifier called a
……………………….
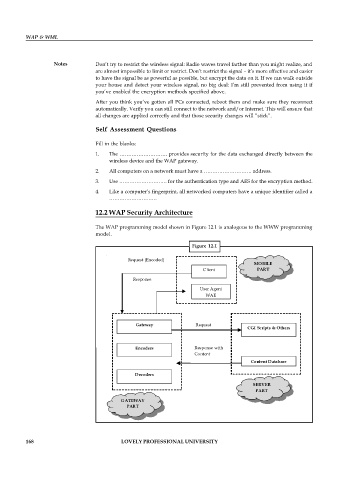
12.2 WAP Security Architecture
The WAP programming model shown in Figure 12.1 is analogous to the WWW programming
model.
Figure 12.1
Request (Encoded)
MOBILE
Client PART
Response
User Agent
WAE
Gateway Request
CGI Scripts & Others
Encoders Response with
Content
Content Database
Decoders
SERVER
PART
GATEWAY
PART
168 LOVELY PROFESSIONAL UNIVERSITY